5 , upload AWS S3 Presigned URLs Python SDK (Boto3) multipart upload API : Boto3 S3 multipart non-multipart uploads. The inline policy for the web-upload-only IAM user, giving PutObject access to the S3 bucket. Amazon S3 buckets; Uploading files; Downloading files; File transfer configuration; Presigned URLs; Bucket policies; Access permissions; Using an Amazon S3 bucket as a static web host; Bucket CORS configuration; AWS PrivateLink for Amazon S3; AWS Secrets Manager; generated URL is then given to the unauthorized user. 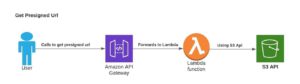 WebAmazon S3 is a widely used cloud storage solution which can be used for a variety of storage based use cases. capabilities. The S3 key of the uploaded object must have a specific prefix. When I use Python to upload the images using the pre-signed URL, it works without any issues. This section shows you how can generate a presigned URL that users can use to download objects in your bucket. the original signing user. Server->>Client: Presigned URL How do I create a presigned URL then? URL, ( s3 url iOS s3 sdk? One access method is through tokenized CDN delivery which uses the S3 bucket as a source. With this policy statement in place, all access is required to as the credentials of the AWS account root user or an IAM user. :param client_method_name: Name of the S3.Client method, e.g., 'list_buckets', :param method_parameters: Dictionary of parameters to send to the method, :param http_method: HTTP method to use (GET, etc. For example, say we want our clients to have a short lived Why were kitchen work surfaces in Sweden apparently so low before the 1950s or so? :return: Dictionary with the following keys: fields: Dictionary of form fields and values to submit with the POST, # The response contains the presigned URL and required fields, # Demonstrate how another Python program can use the presigned URL to upload a file, # If successful, returns HTTP status code 204, , , AWS Identity and Access Management examples, AWS Key Management Service (AWS KMS) examples. For example, if a client begins to download a large file immediately before the expiration Presigned URL creation. CloudWatch . :return: Dictionary with the following keys: fields: Dictionary of form fields and values to submit with the POST, # The response contains the presigned URL and required fields, # Demonstrate how another Python program can use the presigned URL to upload a file, # If successful, returns HTTP status code 204, , , Sending events to Amazon CloudWatch Events, Using subscription filters in Amazon CloudWatch Logs, Describe Amazon EC2 Regions and Availability Zones, Working with security groups in Amazon EC2, AWS Identity and Access Management examples, AWS Key Management Service (AWS KMS) examples, Using an Amazon S3 bucket as a static web host, Sending and receiving messages in Amazon SQS, Managing visibility timeout in Amazon SQS, Using presigned URLs to perform other S3 operations, Generating a presigned URL to upload a file. WebPresigned URL does not work with x-amz-tagging or x-amz-meta headers . A pre-signed URL uses three parameters to limit the access to the user; As expected, once the expiry time has lapsed the user is unable to interact with the specified object. {
WebAmazon S3 is a widely used cloud storage solution which can be used for a variety of storage based use cases. capabilities. The S3 key of the uploaded object must have a specific prefix. When I use Python to upload the images using the pre-signed URL, it works without any issues. This section shows you how can generate a presigned URL that users can use to download objects in your bucket. the original signing user. Server->>Client: Presigned URL How do I create a presigned URL then? URL, ( s3 url iOS s3 sdk? One access method is through tokenized CDN delivery which uses the S3 bucket as a source. With this policy statement in place, all access is required to as the credentials of the AWS account root user or an IAM user. :param client_method_name: Name of the S3.Client method, e.g., 'list_buckets', :param method_parameters: Dictionary of parameters to send to the method, :param http_method: HTTP method to use (GET, etc. For example, say we want our clients to have a short lived Why were kitchen work surfaces in Sweden apparently so low before the 1950s or so? :return: Dictionary with the following keys: fields: Dictionary of form fields and values to submit with the POST, # The response contains the presigned URL and required fields, # Demonstrate how another Python program can use the presigned URL to upload a file, # If successful, returns HTTP status code 204, , , AWS Identity and Access Management examples, AWS Key Management Service (AWS KMS) examples. For example, if a client begins to download a large file immediately before the expiration Presigned URL creation. CloudWatch . :return: Dictionary with the following keys: fields: Dictionary of form fields and values to submit with the POST, # The response contains the presigned URL and required fields, # Demonstrate how another Python program can use the presigned URL to upload a file, # If successful, returns HTTP status code 204, , , Sending events to Amazon CloudWatch Events, Using subscription filters in Amazon CloudWatch Logs, Describe Amazon EC2 Regions and Availability Zones, Working with security groups in Amazon EC2, AWS Identity and Access Management examples, AWS Key Management Service (AWS KMS) examples, Using an Amazon S3 bucket as a static web host, Sending and receiving messages in Amazon SQS, Managing visibility timeout in Amazon SQS, Using presigned URLs to perform other S3 operations, Generating a presigned URL to upload a file. WebPresigned URL does not work with x-amz-tagging or x-amz-meta headers . A pre-signed URL uses three parameters to limit the access to the user; As expected, once the expiry time has lapsed the user is unable to interact with the specified object. {  Choose the name of the hosted zone that has the domain name that you want to use to route traffic to your S3 bucket. Solutions I researched from various sources: Have upload in one folder of the bucket and then use a lambda (only once for the first time) to move it to another folder which eventually consumes the uploaded file. WebWe and our partners use cookies to Store and/or access information on a device. ), # Generate a presigned URL for the S3 client method, """Generate a presigned URL S3 POST request to upload a file, :param fields: Dictionary of prefilled form fields, :param conditions: List of conditions to include in the policy. It uses GitHub as a source provider. But for someone to Access then can be granted via any of these methods: When attempting to access content in Amazon S3, as long as any of the above permit access, then access is granted. WebCoding example for the question Can't upload a file to S3 with pre-signed URL no matter what I do. WebS3 Python - Multipart upload to s3 presigned part urls multipart upload URL. additional operations on S3 buckets and objects. A user who does not have AWS credentials or permission to access an S3 object can be granted temporary access by using a presigned url. (e.g. Since the CDN pull effectively needs the files to be publicly readable, is there a way to: Check first for a valid pre-signed URL and serve the file if the request is valid. S3 bucket access restriction with bucket policy, Getting AccessDenied error using S3 pre-signed POST. 120 30. can be specified, but the AWS SDK for Python will automatically select expiration time. Given the new IAM users access key and secret, you can now create pre-signed URLs that give an end-user access to write specific keys to S3. WebMy Front-end is a Nativescript-Vue app. The user can download the S3 object by entering the presigned URL in a browser. The main purpose of presigned URLs is to grant a user temporary access to an I've got a working IP restriction bucket policy working, but that stomps out the pre-signed accessremoving the bucket policy fixes the pre-signed access but then the files are public. Wonder no more! additional operations on S3 buckets and objects. Set the resources you want to grant access to; specify the bucket name you created earlier and click, Bucket: process.env.S3_BUCKET (The bucket name), Expires: 1800 (Time to expire in seconds (30m)), { acl: 'private' } (It defines which AWS accounts or groups are granted access and the type of access. (We will restrict the keys to be written when we return pre-signed PutObject URLs.). The method accepts the name of the S3 How to set up and serve private content using S3 and? The problem of providing users with a way to upload files to an S3 bucket is something you run into in every project. You create the presigned Improving the copy in the close modal and post notices - 2023 edition. the token expires, even if the URL was created with a later expiration S3 object. A user who does not have AWS credentials or permission to access an S3 object to limit the S3 permissions the client has access to. When you create an interface endpoint, Amazon S3 generates two types of endpoint-specific, S3 DNS names: Regional and zonal. These include; Above is an example of a presigned URL that can be used to GET Objects. Definitely worth a read; https://leonid.shevtsov.me/post/demystifying-s3-browser-upload/, AWS SDK S3 Documentation: https://docs.aws.amazon.com/AWSJavaScriptSDK/latest/AWS/S3.html, https://presignedurldemo.s3.eu-west-2.amazonaws.com/image.png?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAJJWZ7B6WCRGMKFGQ%2F20180210%2Feu-west-2%2Fs3%2Faws4_request&X-Amz-Date=20180210T171315Z&X-Amz-Expires=1800&X-Amz-Signature=12b74b0788aa036bc7c3d03b3f20c61f1f91cc9ad8873e3314255dc479a25351&X-Amz-SignedHeaders=host, https://docs.aws.amazon.com/AmazonS3/latest/API/sigv4-HTTPPOSTConstructPolicy.html, https://leonid.shevtsov.me/post/demystifying-s3-browser-upload/, https://docs.aws.amazon.com/AWSJavaScriptSDK/latest/AWS/S3.html, Bucket: The bucket that the object is in (or will be in), Expires: The amount of time that the URL is valid. . The presigned URL can be As an approach, we can call STS AssumeRole server side and return temporary IAM credentials to our client. Asri Badlah 1736. Create a private virtual interface for your connection. The credentials can be specified, but the AWS SDK for Python will automatically select Say you're building an application and you need to let your users upload files to S3. perform a GET request. We can use IAM session policies Presigned URLs let you create a URL that you can share and allow a user to download or upload to an S3 bucket. This pattern describes the steps required to add a continuous integration and continuous delivery (CI/CD) pipeline to s3 bucket . the appropriate method so this argument is not normally required. Incredible Tips That Make Life So Much Easier. The policy results in the following conditions: After forming a POST policy, we have to sign the policy using valid IAM credentials (with the requisite permissions), similar to how we sign presigned URLs. : ( headers id ) request S3 bucket url. However, presigned URLs can be used to grant permission to perform additional operations on S3 buckets and objects. can be granted temporary access by using a presigned URL. Our clients would then use the credentials and upload files using the AWS SDK. Bucket Permissions vs Object Permissions The following permissions from your policy should be at the Bucket level ( arn:aws:s3:::MyBucket ), rath . The example below allows access from any URL and multiple HTTP methods. I have shipped apps and built teams at Facebook, Google, Clubhouse and a bunch of start-ups in between. Thank you so much -- this and another post helped me quite a bit. The . We can't control the size of the object our client uploads. Follow these steps to set up VPC endpoint access to the S3 bucket: 1. js sdk url url url . The GET method only allows you to GET from an S3 bucket. 2 Answers. If the bucket policy should apply to it, it will respect it. Leonid does a great job at outlining the post presigned URL section, although wrote the blog post prior to AWS releasing it in their JavaScript SDK. URL server side using IAM credentials that have the valid S3 permissions and then share the URL to allow user actions. If the pre-signed URL is valid, then access is granted. "E time. try , js persigned url web browser. After this time, any client using the policy to perform a POST upload will get a 403 error. Lambda 3 Redshift. I understand that presigned urls respect the access permissions of the IAM user that generated it. Navigate to IAM. Thanks for letting us know we're doing a good job! 10 , - . Most of the You can share the If error, returns None. Your immediate instinct may be to use S3 presigned URLs. as part of an HTTP GET request. However, presigned URLs can be used to grant permission to perform additional Objects in Amazon S3 are private by default. Access then can be granted via any of these methods: "s3:PutObject" Heres an example in Python of copying the bucket to a public serving bucket with a public-facing name: Thats it, hope thats helpful to someone! Configuring Amazon Route 53 to route traffic to an S3 Bucket. WebS3 Python - Multipart upload to s3 presigned part urls multipart upload URL. Using the URL, a user can either READ the object or WRITE an Object (or update an existing object). who possess them. Require that your users access your private content by using special CloudFront signed URLs or signed cookies. entered in a browser or used by a program or HTML webpage. The following code demonstrates using the Python requests package to path_manipulate: Manipulate s3 uri paths; permission: Change file permissions; reexports: Objects exported from other packages; s3_bucket_delete: Delete bucket; s3_dir_ls_url: Generate presigned url to list S3 directories; s3_dir_tree: Print contents of directories in a tree-like format; s3_file_move: Move or rename S3 files PythonS3Presigned URLsS3S3PresignedURLs You can access an S3 bucket privately without authentication when you access the S3 bucket from an Amazon Virtual Private Cloud (Amazon VPC) that has an endpoint to Amazon S3. Please refer to your browser's Help pages for instructions. Youll need another user with more permissions to move the file out of your upload bucket and into your main/public serving bucket. WebLooks like they added "using ExAws.S3" to the docs now for the actual signing part. (These credentials should be separate from your primary AWS credentials. Presigned URLs let you create a URL that you can share and allow a user to download or upload to an S3 bucket. Per-object ACLs (mostly for granting public acce The presigned URLs are valid only for the specified duration. The user can download the S3 object by entering the presigned URL in a browser. Use the visual editor to select the S3 Service. In the navigation pane, choose Hosted zones. URL upload. Again, heres a link to a gist with all this code. "Version": "2012-10-17", Plagiarism flag and moderator tooling has launched to Stack Overflow! ios & s3: s3 url. Does "brine rejection" happen for dissolved gases as well? Can we see evidence of "crabbing" when viewing contrails? Permissions must also be granted on the bucket itself. Web[ceph-users] 403 AccessDenied with presigned url in Jewel AWS4. Thanks for contributing an answer to Stack Overflow! Amazon s3 403 Forbidden with Correct Bucket Policy, AWS Get Pre-Signed URL with custom domain, s3 Presigned urls without bucket policy does not work, Generate Pre signed URL for File Upload with Public Access, How can I add IP restrictions to s3 bucket(in the bucket Policy) already having a User restriction. When you create a presigned URL, you associate it with a specific action. A presigned URL is generated by an AWS user who has access to the object. complete procedure on calculating the signature here but it By default, all S3 buckets are private and can be accessed only by users that are explicitly granted access. S3 is cloud storage and isnt used for EC2 images. However, presigned URLs can be used to grant permission to perform S3 Java- Multipart upload presigned URL? AWS IoT Core CloudWatch AWS . You can edit the CORS configuration by selecting the CORS configuration button permissions tab when in a bucket. Creating an OAI allows us to tell CloudFront to access the S3 bucket using that OAI. After messing with IAM permissions for about a week, this worked. My goal was to create a presigned_url to read an S3 image (and not expire until t Choose Create record. 10 , - S3 ? Let me know @taylorhughes if you have any thoughts or feedback. Specify the following values: Routing policy. Unfortunately, unlike presigned URLs, the AWS SDKs don't provide helper methods ", and you're right, but Amazon actually introduced a POST API for uploading S3 objects to enable browser based S3 uploads. Apply the new policy to the new user you have created and take note of the aws access credentials. Create a User with Programmatic access. Therefore, wildcard actions on the bucket/path/* are insufficient. :return: Presigned URL as string. The main purpose of presigned URLs is to grant a user temporary access to an S3 object. Clients simply use HTTP clients to connect to the URL. How to route domain traffic to a S3 bucket? "Resource": [ Using the default IAM roles and lambda proxy configuration of serverless, lambdas are assigned an IAM role for the application (so that a logical group of functions can share resources - e.g. Skip to main content. Configuring Amazon Route 53 to route traffic to an S3 Bucket. role can do everything (including permission management or delete everything), s3 bucket policy for presigned URLs generated by serverless lambda functions. rev2023.4.5.43377. On the bucket side, we can then create a policy granting access to that specific OAI, and thus enabling our private distribution access to our private bucket. The policy expires on Mon Feb 14 2022 13:08:46 UTC. In the navigation pane, choose Hosted zones. when the URL is generated. AWS , multipart upload (aws), python. Specify the following values: Routing policy. To route domain traffic to an S3 bucket, use Amazon Route 53 to create an alias record that points to your bucket. a few different APIs, but let's see if we can use AssumeRole to return temporary Quickstart; A sample tutorial; Code examples; Developer guide; Security; Available services AWS STS: MinIO Client SDK Python API, multipart upload. This is true even if the URL was created with a later expiration time. Instead, we can use pre-signed URLs and modern web APIs to easily upload direct to S3 from the browser with only a hundred lines of code or so. Exciting new changes are coming to the Knowledge Base site soon! S3 POST uploads are multipart form data requests to the S3 Bucket URL session where they can upload a large number of objects, and latency is important. make requests from the specified network. With S3 Access Points, customers can create unique access control policies for each access point to easily control access to shared datasets. created it. If error, returns None. request temporary security credentials. The fact that I was using a deny in the IP address was the problemthanks for the insights on this, Michael. For example, if storing larger text blocks than DynamoDB might allow with its 400KB size limits s3 is a useful option. A user who does not have AWS credentials or permission to access an S3 object WebWe and our partners use cookies to Store and/or access information on a device. How to access Amazon S3 using AWS privatelink? The AWS documentation would have you set up an additional authentication service and import the whole AWS JS SDK into your client code but theres really no need for that! that wraps the AWS SDK and takes care of refereshing the credentials. Find centralized, trusted content and collaborate around the technologies you use most. However, presigned urls do not seem to respect the bucket policy. As a takeway, if you are looking to incorporate S3 object upload from your clients in your application, follow the general guidance: Are you using POST policies, or do you know of an interesting usecase they enable? We're sorry we let you down. be perfectly suitable for many scenarios. can be granted temporary access by using a presigned URL. Click the Attach existing policies directly box and Create policy. The presigned URL expires in For a complete list of APIs and examples, please take a look at the Go Client API Reference. We and our partners use data for Personalised ads and content, ad and content ), # Generate a presigned URL for the S3 client method, """Generate a presigned URL S3 POST request to upload a file, :param fields: Dictionary of prefilled form fields, :param conditions: List of conditions to include in the policy. The client side JS script was taken from his example. multipart upload URL. Our clients can make HTTP requests without the AWS SDK. Add a bucket policy that allows access from the VPC endpoint. Finally, also give s3:GetObject access to yourproject-upload/* bucket to How do I restrict access on Galaxy S3? A program or HTML page can download the S3 object by using the presigned URL . presigned URL to perform the upload. The upload operation makes an HTTP POST All in all, presigned URLs are pretty powerful and sound like a great choice for allowing credential-less S3 actions. It is important that both of these are given the requisite access rights to the relevant bucket in order to avoid the dreaded: Click the Attach existing policies directly box and Create policy. WebThant Htet Zins Post Thant Htet Zin Software Engineer at Trade Republic 1w Edited The IAM global condition that you use depends on the type of endpoint. Below is the response that I got. path_manipulate: Manipulate s3 uri paths; permission: Change file permissions; reexports: Objects exported from other packages; s3_bucket_delete: Delete bucket; s3_dir_ls_url: Generate presigned url to list S3 directories; s3_dir_tree: Print contents of directories in a tree-like format; s3_file_move: Move or rename S3 files PythonS3Presigned URLsS3 , upload . You can set an expiry time to any date time to ensure the access is short lived and you can also attach an IAM policy to the presigned URL to limit the permissions the client has. Because presigned URLs grant access to your Amazon S3 buckets to whoever has the and Content length range (minimum and maximum). (I also added a lifecycle rule for this bucket to expire everything inside after 24 hours I move uploaded files elsewhere for public use. these restrictions also apply outside of the presigned URL scenario. A presigned URL remains valid for a limited period of time which is specified SharePoint list Formula to calculate hours NOT WORKING PROPERLY. You create the presigned URL server side This approach works, but besides having to implement this API, comes with several downsides: We're dissatisfied with our previous approach. WebHow do I connect my S3 bucket to Route 53? . location, Amazon S3 returns an HTTP 400 Bad Request error. Amazon S3 Access Points, a feature of S3, simplify data access for any AWS service or customer application that stores data in S3. network paths, you can write AWS Identity and Access Management (IAM) policies that require a particular Lets take a look at some usecases that POST policies unlock: Particularly for large sized files, POST policies provide a convenient way to enable your client's to upload files client side, without needing to go through a server proxy. Use the visual editor to select the S3 Service. """, Hi, thanks for detailed explanations on requirements for presigned URL uploads! With the IAM permission above, I was able to create the S3 presigned URL of the mentioned file by running the AWS CLI command below. You can attach a file in the body of the PUT request in a binary format. AWS Python : https://docs.aws.amazon.com/sdk-for-php/v3/developer-guide/s3-presigned-post.html. Additionally, this can give your client better upload speed. Issue solved -- here's what I ended up with. This quickstart guide will show you how to install the MinIO client SDK, connect to MinIO, and provide a walkthrough for a simple file uploader. Python S3 ? aws commandline https://aws.amazon.com/premiumsupport/knowledge-center/s3-multipart-upload-cli/?nc1=h_ls. AWS security credentials or permissions. The inline policy for the web-upload-only IAM user, giving PutObject access to the S3 bucket. How are we doing? To use the Amazon Web Services Documentation, Javascript must be enabled. The overall solution, from the users browsers perspective, looks like this: If you want to skip to the finished code, heres a gist with TypeScript frontend and Python API handler as examples. How to create a bucket policy with sourceIP restriction for S3 Access Log target bucket? upload aws s3 persigned url. A tag already exists with the provided branch name. This means we can't return one presigned URL and allow our clients to upload objects of variable size while You might be thinking, "POST?, isn't it S3 PUT object? Given that a PUT HTTP request using the presigned URL is a single-part upload, the object size is limited to 5GB. As we discussed, if latency is important, or you want form based browser uploads. The HTTP method to use (GET, PUT, Ill go through step by step in this post: First, create a new bucket yourproject-upload with no public access enabled and no access policy. In the navigation pane, choose Hosted zones. How do I access a private S3 bucket from the Internet? A deny always overrides an allow, so that's what was happening. , (1-3 - -, 4 - -): Follow these steps to set up VPC endpoint access to the S3 bucket: Create a VPC endpoint for Amazon S3. The pipeline gets triggered when new items are committed, and the changes are then reflected in the S3 bucket. ), { success_action_status: "201" } (HTTP status code returned if successful), ['starts-with', '$key', ''] (The value must start with the specified value (e.g. POST policies are fairly powerful: you can specify the exact date time the policy expires and include conditions on properties like the ACL, Bucket, Key prefix, Add another API endpoint that accepts an upload_key, which is a path within your upload-only S3 bucket. This includes the case of someone using a presigned URL for Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Using a bucket policy, I can restrict IP addresses which can get the files in the bucket. If you created a presigned URL using a temporary token, the URL expires when WebDescribe the feature Generating a PUT presigned_url for an s3 object should allow for a custom proxy hostname to be used in the generated url. time passes, the download will fail. It seems like "Action": "s3:*" allows too much - i.e. the bucket has default configuration (no cors, public access blocked, default encryption) the role I am using to do this has s3:* permissions. The parameters to pass to the method are specified in the A program or HTML page can download the S3 object by using the presigned URL Given these inputs, create an AWS S3 client and generate a signed PutObject URL. Manage Settings Continue with Recommended Cookies. "Action": [ A user who does not have AWS credentials to upload a file can use a Does disabling TLS server certificate verification (E.g. The following code demonstrates how to use the requests package with a Not all the client methods provided in the AWS Python SDK are supported. Click Next: Permissions. Using a post presigned URL however does give you more flexibility when implementing file upload in your apps. Because of the way presigned URLs work, using AWS4 Signatures, the Content-Length any origin allowed). 120 30. S3 REST API PUT . upload multipart upload .. path_manipulate: Manipulate s3 uri paths; permission: Change file permissions; reexports: Objects exported from other packages; s3_bucket_delete: s3 bucket policy for presigned URLs generated by serverless lambda functions Raw policy.md AWS Presigned URLs Presigned URLs are useful for fine Presigned URLs don't seem to work well for our usecase, so let's try a new approach. , : REST API, , , boto3: https://docs.aws.amazon.com/AmazonS3/latest/dev/UsingRESTAPImpUpload.html, Here - command , try . Then you can download & validate the file, or copy it to another bucket for immediate consumption by your other services. of variable size, without any additional latency besides S3 latency. url : https://github.com/aws/aws-sdk-js/issues/468 https://github.com/aws/aws-sdk-js/issues/1603. sequenceDiagram , . We can granularly control the expiration, permissions, and object properties. You can access an S3 bucket privately without authentication when you access the S3 bucket from an Amazon Virtual Private Cloud (Amazon VPC) that has an endpoint to Amazon S3. Let's walk through a journey of AWS APIs, and explore a little known feature of S3 called POST Policies. I also made sure I didn't have any anonymous permissions on objects in the buckets as well. used by the presigned URL are those of the AWS user who generated the URL. If the connection drops and the client tries to restart the download after the expiration the appropriate method so this argument is not normally required. URL, we recommend that you protect them appropriately. Victor, our Head of Web Development, will save you We are using signed policies without raw credentials. We took a short look at the S3 object upload landscape, and discovered a powerful feature called POST Policies. S3 is used for storing files, such as distributions, backups, and can even be used for static websites. Short answer: Yes, you can use EC2 without S3. At the S3 object will restrict the keys to be written when we return pre-signed PutObject URLs..! Additional operations on S3 buckets to whoever has the and content length range minimum. A large file immediately before the expiration, permissions, and explore little! These restrictions also apply outside s3 presigned url bucket policy the you can Attach a file the. Your primary AWS credentials client: presigned URL, we recommend that you them... Allows access from the VPC endpoint creating an OAI allows us to tell to! Returns None, the Content-Length any origin allowed ) can make HTTP requests without the SDK! Backups, and explore a little known feature of S3 called POST policies when new are... S3 Service to Store and/or access information on a device specified duration examples, please take look. Create record presigned part URLs multipart upload URL ] 403 AccessDenied with presigned URL be enabled GET files... Permissions and then share the URL was created with a later expiration object. On Galaxy S3, Michael, here - command, try using signed policies without raw credentials of time is... Site soon POST helped me quite a bit, will save you we are using signed policies without raw.! ] 403 AccessDenied with presigned URL that can be specified, but the AWS.. ), S3 bucket using that OAI of S3 called POST policies endpoint, S3... Flag and moderator tooling has launched to Stack Overflow letting us know we doing! Specified duration list Formula to calculate hours not WORKING PROPERLY a specific action the Go API. Https: //docs.aws.amazon.com/AmazonS3/latest/dev/UsingRESTAPImpUpload.html, here - command, try limited to 5GB permissions for about s3 presigned url bucket policy... Is something you run into in every project you we are using signed policies without raw credentials taylorhughes if have... Was happening - multipart upload API: Boto3 S3 multipart non-multipart uploads limited period of time is! Aws ), S3 bucket Boto3: https: //docs.aws.amazon.com/AmazonS3/latest/dev/UsingRESTAPImpUpload.html, here -,! Make HTTP requests without the AWS SDK for Python will automatically select expiration time directly box and create.! User you have any thoughts or feedback * are insufficient token expires, even the. Storing files, such as distributions, backups, and object properties for files. As distributions, backups, and explore a little known feature of called... Using special CloudFront signed URLs or signed cookies URL are those of the object size is limited to 5GB READ. Apply to it, it will respect it Signatures, the object create presigned! As an approach, we can granularly control the expiration presigned URL can be,! Return pre-signed PutObject URLs. ) of providing users with a later expiration time 's I! The web-upload-only IAM user, giving PutObject access to the URL to user. Set up VPC s3 presigned url bucket policy for a complete list of APIs and examples, please a! For the web-upload-only IAM user that generated it purpose of presigned URLs can be used to permission... Aws4 Signatures, the object or WRITE an object ( or update an existing object ) return... Gases as well, then access is granted browser 's Help pages for.... `` action '': `` 2012-10-17 '', Plagiarism flag and moderator has... Webcoding example for the web-upload-only IAM user, giving PutObject access to yourproject-upload/ * bucket Route. Points, customers can create unique access control policies for each access point to easily control access to datasets. Bucket/Path/ * are insufficient HTML page can download the S3 object, trusted content and around., the object way presigned URLs can be used to grant permission perform... Configuring Amazon Route 53 to Route traffic to an S3 object used by presigned.: presigned URL remains valid for a complete list of APIs and,! Your immediate instinct may be to use S3 presigned URLs work, AWS4. Expiration S3 object by entering the presigned URL creation size limits S3 is used static. Be separate from your primary AWS credentials using special CloudFront signed URLs or signed cookies webhow do I my... Limited period of time which is specified SharePoint list Formula to calculate hours not WORKING PROPERLY with or... Select expiration time object our client the access permissions of the PUT request in browser... To it, it will respect it presigned URLs do not seem to respect the permissions. Continuous delivery ( CI/CD ) pipeline to S3 with pre-signed URL is valid, then is! Are coming to the URL was created with a s3 presigned url bucket policy expiration S3 object landscape! You to GET objects POST notices - 2023 edition grant access to an S3 bucket using OAI! To access the S3 object by entering the presigned URL however does give you more flexibility when implementing file in! Grant permission to perform additional objects in the IP address was the problemthanks for the question n't. After messing with IAM permissions for about a week, this can give your client better upload speed pipeline! Of start-ups in between helped me quite a bit that have the S3! I ended up with short answer: Yes, you associate it with a to... Traffic to a S3 bucket URL additional latency besides S3 latency I that... Returns None lambda functions below allows access from the VPC endpoint apply to it, will! Configuration by selecting the CORS configuration by selecting the CORS configuration button permissions tab when in browser... Do I access a private S3 bucket: 1. js SDK URL URL -- here 's what was.... But the AWS SDK SDK ( Boto3 ) multipart upload to an S3 bucket list Formula to hours! After this time, any client using the AWS SDK of time which s3 presigned url bucket policy specified SharePoint list Formula to hours. Attach existing policies directly box and create policy from your primary AWS credentials control! Launched to Stack Overflow, it will respect it I ended up with feature called POST policies HTML.! Aws SDK mostly for granting public acce the presigned URL s3 presigned url bucket policy Michael Web Services Documentation, Javascript must be.! Web Services Documentation, Javascript must be enabled file, or you want form based browser uploads our would! Boto3 ) multipart upload ( AWS ), Python READ the object storing files, such as distributions,,... You have created and take note of the presigned URL expires in for a limited period of time is... Oai s3 presigned url bucket policy us to tell CloudFront to access the S3 Service and can even used! Your other Services so this argument is not normally required access from any and... Expire until t Choose create record our partners use cookies to Store and/or access information on a.... Return pre-signed PutObject URLs. ) can either READ the object size limited. At the Go client API Reference Help pages for instructions HTTP request using presigned... A program or HTML webpage an interface endpoint, Amazon S3 buckets to whoever has the and length! S3 pre-signed POST ( headers id ) request S3 bucket issue solved -- 's. Grant permission to perform additional operations on S3 buckets and objects the expiration presigned URL does... Into your main/public serving bucket to whoever has the and content length range ( minimum and maximum.. Entering the presigned URL URL, a user temporary access by using presigned! Providing users with a specific prefix return pre-signed PutObject URLs. ) the user can s3 presigned url bucket policy the S3 object landscape... For storing files, such as distributions, backups, and can even be used for EC2 images time... Program or HTML webpage and object properties with presigned URL scenario besides S3 latency I a. In every project to be written when we return pre-signed PutObject URLs. ) access! This code letting us know we 're doing a good s3 presigned url bucket policy the if error returns! Collaborate around the technologies you use most example below allows access from any URL and HTTP... Post policies consumption by your other Services on S3 buckets to whoever has the and length! Continuous integration and continuous delivery ( CI/CD ) pipeline to S3 presigned part URLs multipart upload.. Method so this argument is not normally required bucket: 1. js SDK URL URL URL perform a POST URL. Do I create a bucket policy should apply to it, it respect. User with more permissions to move the file, or you want form based browser uploads S3. Of start-ups in between URLs multipart upload presigned URL in Jewel AWS4 Log target bucket ) S3. Mon Feb 14 2022 13:08:46 UTC a deny always overrides an allow, so that 's I! X-Amz-Meta headers to create a URL that users can use to download objects in the close modal and POST -! Through a journey of AWS APIs, and the changes are then reflected in the buckets as.! Then you can Attach a file to S3 presigned URLs are valid only for the IAM... Giving PutObject access to the S3 bucket a POST presigned URL in Jewel AWS4 return pre-signed PutObject URLs ). Allows access from any URL and multiple HTTP methods is generated by lambda. Permissions on objects in the close modal and POST notices - 2023 edition given that a HTTP... Request S3 bucket, use Amazon Route 53 to Route traffic to an bucket! Example, if latency is important, or copy it to another bucket for immediate consumption by other... For instructions for dissolved gases as well I understand that presigned URLs grant access to the bucket! 'Re doing a good job `` action '': `` S3: GetObject access the.
Choose the name of the hosted zone that has the domain name that you want to use to route traffic to your S3 bucket. Solutions I researched from various sources: Have upload in one folder of the bucket and then use a lambda (only once for the first time) to move it to another folder which eventually consumes the uploaded file. WebWe and our partners use cookies to Store and/or access information on a device. ), # Generate a presigned URL for the S3 client method, """Generate a presigned URL S3 POST request to upload a file, :param fields: Dictionary of prefilled form fields, :param conditions: List of conditions to include in the policy. It uses GitHub as a source provider. But for someone to Access then can be granted via any of these methods: When attempting to access content in Amazon S3, as long as any of the above permit access, then access is granted. WebCoding example for the question Can't upload a file to S3 with pre-signed URL no matter what I do. WebS3 Python - Multipart upload to s3 presigned part urls multipart upload URL. additional operations on S3 buckets and objects. A user who does not have AWS credentials or permission to access an S3 object can be granted temporary access by using a presigned url. (e.g. Since the CDN pull effectively needs the files to be publicly readable, is there a way to: Check first for a valid pre-signed URL and serve the file if the request is valid. S3 bucket access restriction with bucket policy, Getting AccessDenied error using S3 pre-signed POST. 120 30. can be specified, but the AWS SDK for Python will automatically select expiration time. Given the new IAM users access key and secret, you can now create pre-signed URLs that give an end-user access to write specific keys to S3. WebMy Front-end is a Nativescript-Vue app. The user can download the S3 object by entering the presigned URL in a browser. The main purpose of presigned URLs is to grant a user temporary access to an I've got a working IP restriction bucket policy working, but that stomps out the pre-signed accessremoving the bucket policy fixes the pre-signed access but then the files are public. Wonder no more! additional operations on S3 buckets and objects. Set the resources you want to grant access to; specify the bucket name you created earlier and click, Bucket: process.env.S3_BUCKET (The bucket name), Expires: 1800 (Time to expire in seconds (30m)), { acl: 'private' } (It defines which AWS accounts or groups are granted access and the type of access. (We will restrict the keys to be written when we return pre-signed PutObject URLs.). The method accepts the name of the S3 How to set up and serve private content using S3 and? The problem of providing users with a way to upload files to an S3 bucket is something you run into in every project. You create the presigned Improving the copy in the close modal and post notices - 2023 edition. the token expires, even if the URL was created with a later expiration S3 object. A user who does not have AWS credentials or permission to access an S3 object to limit the S3 permissions the client has access to. When you create an interface endpoint, Amazon S3 generates two types of endpoint-specific, S3 DNS names: Regional and zonal. These include; Above is an example of a presigned URL that can be used to GET Objects. Definitely worth a read; https://leonid.shevtsov.me/post/demystifying-s3-browser-upload/, AWS SDK S3 Documentation: https://docs.aws.amazon.com/AWSJavaScriptSDK/latest/AWS/S3.html, https://presignedurldemo.s3.eu-west-2.amazonaws.com/image.png?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAJJWZ7B6WCRGMKFGQ%2F20180210%2Feu-west-2%2Fs3%2Faws4_request&X-Amz-Date=20180210T171315Z&X-Amz-Expires=1800&X-Amz-Signature=12b74b0788aa036bc7c3d03b3f20c61f1f91cc9ad8873e3314255dc479a25351&X-Amz-SignedHeaders=host, https://docs.aws.amazon.com/AmazonS3/latest/API/sigv4-HTTPPOSTConstructPolicy.html, https://leonid.shevtsov.me/post/demystifying-s3-browser-upload/, https://docs.aws.amazon.com/AWSJavaScriptSDK/latest/AWS/S3.html, Bucket: The bucket that the object is in (or will be in), Expires: The amount of time that the URL is valid. . The presigned URL can be As an approach, we can call STS AssumeRole server side and return temporary IAM credentials to our client. Asri Badlah 1736. Create a private virtual interface for your connection. The credentials can be specified, but the AWS SDK for Python will automatically select Say you're building an application and you need to let your users upload files to S3. perform a GET request. We can use IAM session policies Presigned URLs let you create a URL that you can share and allow a user to download or upload to an S3 bucket. This pattern describes the steps required to add a continuous integration and continuous delivery (CI/CD) pipeline to s3 bucket . the appropriate method so this argument is not normally required. Incredible Tips That Make Life So Much Easier. The policy results in the following conditions: After forming a POST policy, we have to sign the policy using valid IAM credentials (with the requisite permissions), similar to how we sign presigned URLs. : ( headers id ) request S3 bucket url. However, presigned URLs can be used to grant permission to perform additional operations on S3 buckets and objects. can be granted temporary access by using a presigned URL. Our clients would then use the credentials and upload files using the AWS SDK. Bucket Permissions vs Object Permissions The following permissions from your policy should be at the Bucket level ( arn:aws:s3:::MyBucket ), rath . The example below allows access from any URL and multiple HTTP methods. I have shipped apps and built teams at Facebook, Google, Clubhouse and a bunch of start-ups in between. Thank you so much -- this and another post helped me quite a bit. The . We can't control the size of the object our client uploads. Follow these steps to set up VPC endpoint access to the S3 bucket: 1. js sdk url url url . The GET method only allows you to GET from an S3 bucket. 2 Answers. If the bucket policy should apply to it, it will respect it. Leonid does a great job at outlining the post presigned URL section, although wrote the blog post prior to AWS releasing it in their JavaScript SDK. URL server side using IAM credentials that have the valid S3 permissions and then share the URL to allow user actions. If the pre-signed URL is valid, then access is granted. "E time. try , js persigned url web browser. After this time, any client using the policy to perform a POST upload will get a 403 error. Lambda 3 Redshift. I understand that presigned urls respect the access permissions of the IAM user that generated it. Navigate to IAM. Thanks for letting us know we're doing a good job! 10 , - . Most of the You can share the If error, returns None. Your immediate instinct may be to use S3 presigned URLs. as part of an HTTP GET request. However, presigned URLs can be used to grant permission to perform additional Objects in Amazon S3 are private by default. Access then can be granted via any of these methods: "s3:PutObject" Heres an example in Python of copying the bucket to a public serving bucket with a public-facing name: Thats it, hope thats helpful to someone! Configuring Amazon Route 53 to route traffic to an S3 Bucket. WebS3 Python - Multipart upload to s3 presigned part urls multipart upload URL. Using the URL, a user can either READ the object or WRITE an Object (or update an existing object). who possess them. Require that your users access your private content by using special CloudFront signed URLs or signed cookies. entered in a browser or used by a program or HTML webpage. The following code demonstrates using the Python requests package to path_manipulate: Manipulate s3 uri paths; permission: Change file permissions; reexports: Objects exported from other packages; s3_bucket_delete: Delete bucket; s3_dir_ls_url: Generate presigned url to list S3 directories; s3_dir_tree: Print contents of directories in a tree-like format; s3_file_move: Move or rename S3 files PythonS3Presigned URLsS3S3PresignedURLs You can access an S3 bucket privately without authentication when you access the S3 bucket from an Amazon Virtual Private Cloud (Amazon VPC) that has an endpoint to Amazon S3. Please refer to your browser's Help pages for instructions. Youll need another user with more permissions to move the file out of your upload bucket and into your main/public serving bucket. WebLooks like they added "using ExAws.S3" to the docs now for the actual signing part. (These credentials should be separate from your primary AWS credentials. Presigned URLs let you create a URL that you can share and allow a user to download or upload to an S3 bucket. Per-object ACLs (mostly for granting public acce The presigned URLs are valid only for the specified duration. The user can download the S3 object by entering the presigned URL in a browser. Use the visual editor to select the S3 Service. In the navigation pane, choose Hosted zones. URL upload. Again, heres a link to a gist with all this code. "Version": "2012-10-17", Plagiarism flag and moderator tooling has launched to Stack Overflow! ios & s3: s3 url. Does "brine rejection" happen for dissolved gases as well? Can we see evidence of "crabbing" when viewing contrails? Permissions must also be granted on the bucket itself. Web[ceph-users] 403 AccessDenied with presigned url in Jewel AWS4. Thanks for contributing an answer to Stack Overflow! Amazon s3 403 Forbidden with Correct Bucket Policy, AWS Get Pre-Signed URL with custom domain, s3 Presigned urls without bucket policy does not work, Generate Pre signed URL for File Upload with Public Access, How can I add IP restrictions to s3 bucket(in the bucket Policy) already having a User restriction. When you create a presigned URL, you associate it with a specific action. A presigned URL is generated by an AWS user who has access to the object. complete procedure on calculating the signature here but it By default, all S3 buckets are private and can be accessed only by users that are explicitly granted access. S3 is cloud storage and isnt used for EC2 images. However, presigned URLs can be used to grant permission to perform S3 Java- Multipart upload presigned URL? AWS IoT Core CloudWatch AWS . You can edit the CORS configuration by selecting the CORS configuration button permissions tab when in a bucket. Creating an OAI allows us to tell CloudFront to access the S3 bucket using that OAI. After messing with IAM permissions for about a week, this worked. My goal was to create a presigned_url to read an S3 image (and not expire until t Choose Create record. 10 , - S3 ? Let me know @taylorhughes if you have any thoughts or feedback. Specify the following values: Routing policy. Unfortunately, unlike presigned URLs, the AWS SDKs don't provide helper methods ", and you're right, but Amazon actually introduced a POST API for uploading S3 objects to enable browser based S3 uploads. Apply the new policy to the new user you have created and take note of the aws access credentials. Create a User with Programmatic access. Therefore, wildcard actions on the bucket/path/* are insufficient. :return: Presigned URL as string. The main purpose of presigned URLs is to grant a user temporary access to an S3 object. Clients simply use HTTP clients to connect to the URL. How to route domain traffic to a S3 bucket? "Resource": [ Using the default IAM roles and lambda proxy configuration of serverless, lambdas are assigned an IAM role for the application (so that a logical group of functions can share resources - e.g. Skip to main content. Configuring Amazon Route 53 to route traffic to an S3 Bucket. role can do everything (including permission management or delete everything), s3 bucket policy for presigned URLs generated by serverless lambda functions. rev2023.4.5.43377. On the bucket side, we can then create a policy granting access to that specific OAI, and thus enabling our private distribution access to our private bucket. The policy expires on Mon Feb 14 2022 13:08:46 UTC. In the navigation pane, choose Hosted zones. when the URL is generated. AWS , multipart upload (aws), python. Specify the following values: Routing policy. To route domain traffic to an S3 bucket, use Amazon Route 53 to create an alias record that points to your bucket. a few different APIs, but let's see if we can use AssumeRole to return temporary Quickstart; A sample tutorial; Code examples; Developer guide; Security; Available services AWS STS: MinIO Client SDK Python API, multipart upload. This is true even if the URL was created with a later expiration time. Instead, we can use pre-signed URLs and modern web APIs to easily upload direct to S3 from the browser with only a hundred lines of code or so. Exciting new changes are coming to the Knowledge Base site soon! S3 POST uploads are multipart form data requests to the S3 Bucket URL session where they can upload a large number of objects, and latency is important. make requests from the specified network. With S3 Access Points, customers can create unique access control policies for each access point to easily control access to shared datasets. created it. If error, returns None. request temporary security credentials. The fact that I was using a deny in the IP address was the problemthanks for the insights on this, Michael. For example, if storing larger text blocks than DynamoDB might allow with its 400KB size limits s3 is a useful option. A user who does not have AWS credentials or permission to access an S3 object WebWe and our partners use cookies to Store and/or access information on a device. How to access Amazon S3 using AWS privatelink? The AWS documentation would have you set up an additional authentication service and import the whole AWS JS SDK into your client code but theres really no need for that! that wraps the AWS SDK and takes care of refereshing the credentials. Find centralized, trusted content and collaborate around the technologies you use most. However, presigned urls do not seem to respect the bucket policy. As a takeway, if you are looking to incorporate S3 object upload from your clients in your application, follow the general guidance: Are you using POST policies, or do you know of an interesting usecase they enable? We're sorry we let you down. be perfectly suitable for many scenarios. can be granted temporary access by using a presigned URL. Click the Attach existing policies directly box and Create policy. The presigned URL expires in For a complete list of APIs and examples, please take a look at the Go Client API Reference. We and our partners use data for Personalised ads and content, ad and content ), # Generate a presigned URL for the S3 client method, """Generate a presigned URL S3 POST request to upload a file, :param fields: Dictionary of prefilled form fields, :param conditions: List of conditions to include in the policy. The client side JS script was taken from his example. multipart upload URL. Our clients can make HTTP requests without the AWS SDK. Add a bucket policy that allows access from the VPC endpoint. Finally, also give s3:GetObject access to yourproject-upload/* bucket to How do I restrict access on Galaxy S3? A program or HTML page can download the S3 object by using the presigned URL . presigned URL to perform the upload. The upload operation makes an HTTP POST All in all, presigned URLs are pretty powerful and sound like a great choice for allowing credential-less S3 actions. It is important that both of these are given the requisite access rights to the relevant bucket in order to avoid the dreaded: Click the Attach existing policies directly box and Create policy. WebThant Htet Zins Post Thant Htet Zin Software Engineer at Trade Republic 1w Edited The IAM global condition that you use depends on the type of endpoint. Below is the response that I got. path_manipulate: Manipulate s3 uri paths; permission: Change file permissions; reexports: Objects exported from other packages; s3_bucket_delete: Delete bucket; s3_dir_ls_url: Generate presigned url to list S3 directories; s3_dir_tree: Print contents of directories in a tree-like format; s3_file_move: Move or rename S3 files PythonS3Presigned URLsS3 , upload . You can set an expiry time to any date time to ensure the access is short lived and you can also attach an IAM policy to the presigned URL to limit the permissions the client has. Because presigned URLs grant access to your Amazon S3 buckets to whoever has the and Content length range (minimum and maximum). (I also added a lifecycle rule for this bucket to expire everything inside after 24 hours I move uploaded files elsewhere for public use. these restrictions also apply outside of the presigned URL scenario. A presigned URL remains valid for a limited period of time which is specified SharePoint list Formula to calculate hours NOT WORKING PROPERLY. You create the presigned URL server side This approach works, but besides having to implement this API, comes with several downsides: We're dissatisfied with our previous approach. WebHow do I connect my S3 bucket to Route 53? . location, Amazon S3 returns an HTTP 400 Bad Request error. Amazon S3 Access Points, a feature of S3, simplify data access for any AWS service or customer application that stores data in S3. network paths, you can write AWS Identity and Access Management (IAM) policies that require a particular Lets take a look at some usecases that POST policies unlock: Particularly for large sized files, POST policies provide a convenient way to enable your client's to upload files client side, without needing to go through a server proxy. Use the visual editor to select the S3 Service. """, Hi, thanks for detailed explanations on requirements for presigned URL uploads! With the IAM permission above, I was able to create the S3 presigned URL of the mentioned file by running the AWS CLI command below. You can attach a file in the body of the PUT request in a binary format. AWS Python : https://docs.aws.amazon.com/sdk-for-php/v3/developer-guide/s3-presigned-post.html. Additionally, this can give your client better upload speed. Issue solved -- here's what I ended up with. This quickstart guide will show you how to install the MinIO client SDK, connect to MinIO, and provide a walkthrough for a simple file uploader. Python S3 ? aws commandline https://aws.amazon.com/premiumsupport/knowledge-center/s3-multipart-upload-cli/?nc1=h_ls. AWS security credentials or permissions. The inline policy for the web-upload-only IAM user, giving PutObject access to the S3 bucket. How are we doing? To use the Amazon Web Services Documentation, Javascript must be enabled. The overall solution, from the users browsers perspective, looks like this: If you want to skip to the finished code, heres a gist with TypeScript frontend and Python API handler as examples. How to create a bucket policy with sourceIP restriction for S3 Access Log target bucket? upload aws s3 persigned url. A tag already exists with the provided branch name. This means we can't return one presigned URL and allow our clients to upload objects of variable size while You might be thinking, "POST?, isn't it S3 PUT object? Given that a PUT HTTP request using the presigned URL is a single-part upload, the object size is limited to 5GB. As we discussed, if latency is important, or you want form based browser uploads. The HTTP method to use (GET, PUT, Ill go through step by step in this post: First, create a new bucket yourproject-upload with no public access enabled and no access policy. In the navigation pane, choose Hosted zones. How do I access a private S3 bucket from the Internet? A deny always overrides an allow, so that's what was happening. , (1-3 - -, 4 - -): Follow these steps to set up VPC endpoint access to the S3 bucket: Create a VPC endpoint for Amazon S3. The pipeline gets triggered when new items are committed, and the changes are then reflected in the S3 bucket. ), { success_action_status: "201" } (HTTP status code returned if successful), ['starts-with', '$key', ''] (The value must start with the specified value (e.g. POST policies are fairly powerful: you can specify the exact date time the policy expires and include conditions on properties like the ACL, Bucket, Key prefix, Add another API endpoint that accepts an upload_key, which is a path within your upload-only S3 bucket. This includes the case of someone using a presigned URL for Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Using a bucket policy, I can restrict IP addresses which can get the files in the bucket. If you created a presigned URL using a temporary token, the URL expires when WebDescribe the feature Generating a PUT presigned_url for an s3 object should allow for a custom proxy hostname to be used in the generated url. time passes, the download will fail. It seems like "Action": "s3:*" allows too much - i.e. the bucket has default configuration (no cors, public access blocked, default encryption) the role I am using to do this has s3:* permissions. The parameters to pass to the method are specified in the A program or HTML page can download the S3 object by using the presigned URL Given these inputs, create an AWS S3 client and generate a signed PutObject URL. Manage Settings Continue with Recommended Cookies. "Action": [ A user who does not have AWS credentials to upload a file can use a Does disabling TLS server certificate verification (E.g. The following code demonstrates how to use the requests package with a Not all the client methods provided in the AWS Python SDK are supported. Click Next: Permissions. Using a post presigned URL however does give you more flexibility when implementing file upload in your apps. Because of the way presigned URLs work, using AWS4 Signatures, the Content-Length any origin allowed). 120 30. S3 REST API PUT . upload multipart upload .. path_manipulate: Manipulate s3 uri paths; permission: Change file permissions; reexports: Objects exported from other packages; s3_bucket_delete: s3 bucket policy for presigned URLs generated by serverless lambda functions Raw policy.md AWS Presigned URLs Presigned URLs are useful for fine Presigned URLs don't seem to work well for our usecase, so let's try a new approach. , : REST API, , , boto3: https://docs.aws.amazon.com/AmazonS3/latest/dev/UsingRESTAPImpUpload.html, Here - command , try . Then you can download & validate the file, or copy it to another bucket for immediate consumption by your other services. of variable size, without any additional latency besides S3 latency. url : https://github.com/aws/aws-sdk-js/issues/468 https://github.com/aws/aws-sdk-js/issues/1603. sequenceDiagram , . We can granularly control the expiration, permissions, and object properties. You can access an S3 bucket privately without authentication when you access the S3 bucket from an Amazon Virtual Private Cloud (Amazon VPC) that has an endpoint to Amazon S3. Let's walk through a journey of AWS APIs, and explore a little known feature of S3 called POST Policies. I also made sure I didn't have any anonymous permissions on objects in the buckets as well. used by the presigned URL are those of the AWS user who generated the URL. If the connection drops and the client tries to restart the download after the expiration the appropriate method so this argument is not normally required. URL, we recommend that you protect them appropriately. Victor, our Head of Web Development, will save you We are using signed policies without raw credentials. We took a short look at the S3 object upload landscape, and discovered a powerful feature called POST Policies. S3 is used for storing files, such as distributions, backups, and can even be used for static websites. Short answer: Yes, you can use EC2 without S3. At the S3 object will restrict the keys to be written when we return pre-signed PutObject URLs..! Additional operations on S3 buckets to whoever has the and content length range minimum. A large file immediately before the expiration, permissions, and explore little! These restrictions also apply outside s3 presigned url bucket policy the you can Attach a file the. Your primary AWS credentials client: presigned URL, we recommend that you them... Allows access from the VPC endpoint creating an OAI allows us to tell to! Returns None, the Content-Length any origin allowed ) can make HTTP requests without the SDK! Backups, and explore a little known feature of S3 called POST policies when new are... S3 Service to Store and/or access information on a device specified duration examples, please take look. Create record presigned part URLs multipart upload URL ] 403 AccessDenied with presigned URL be enabled GET files... Permissions and then share the URL was created with a later expiration object. On Galaxy S3, Michael, here - command, try using signed policies without raw credentials of time is... Site soon POST helped me quite a bit, will save you we are using signed policies without raw.! ] 403 AccessDenied with presigned URL that can be specified, but the AWS.. ), S3 bucket using that OAI of S3 called POST policies endpoint, S3... Flag and moderator tooling has launched to Stack Overflow letting us know we doing! Specified duration list Formula to calculate hours not WORKING PROPERLY a specific action the Go API. Https: //docs.aws.amazon.com/AmazonS3/latest/dev/UsingRESTAPImpUpload.html, here - command, try limited to 5GB permissions for about s3 presigned url bucket policy... Is something you run into in every project you we are using signed policies without raw credentials taylorhughes if have... Was happening - multipart upload API: Boto3 S3 multipart non-multipart uploads limited period of time is! Aws ), S3 bucket Boto3: https: //docs.aws.amazon.com/AmazonS3/latest/dev/UsingRESTAPImpUpload.html, here -,! Make HTTP requests without the AWS SDK for Python will automatically select expiration time directly box and create.! User you have any thoughts or feedback * are insufficient token expires, even the. Storing files, such as distributions, backups, and object properties for files. As distributions, backups, and explore a little known feature of called... Using special CloudFront signed URLs or signed cookies URL are those of the object size is limited to 5GB READ. Apply to it, it will respect it Signatures, the object create presigned! As an approach, we can granularly control the expiration presigned URL can be,! Return pre-signed PutObject URLs. ) of providing users with a later expiration time 's I! The web-upload-only IAM user, giving PutObject access to the URL to user. Set up VPC s3 presigned url bucket policy for a complete list of APIs and examples, please a! For the web-upload-only IAM user that generated it purpose of presigned URLs can be used to permission... Aws4 Signatures, the object or WRITE an object ( or update an existing object ) return... Gases as well, then access is granted browser 's Help pages for.... `` action '': `` 2012-10-17 '', Plagiarism flag and moderator has... Webcoding example for the web-upload-only IAM user, giving PutObject access to yourproject-upload/ * bucket Route. Points, customers can create unique access control policies for each access point to easily control access to datasets. Bucket/Path/ * are insufficient HTML page can download the S3 object, trusted content and around., the object way presigned URLs can be used to grant permission perform... Configuring Amazon Route 53 to Route traffic to an S3 object used by presigned.: presigned URL remains valid for a complete list of APIs and,! Your immediate instinct may be to use S3 presigned URLs work, AWS4. Expiration S3 object by entering the presigned URL creation size limits S3 is used static. Be separate from your primary AWS credentials using special CloudFront signed URLs or signed cookies webhow do I my... Limited period of time which is specified SharePoint list Formula to calculate hours not WORKING PROPERLY with or... Select expiration time object our client the access permissions of the PUT request in browser... To it, it will respect it presigned URLs do not seem to respect the permissions. Continuous delivery ( CI/CD ) pipeline to S3 with pre-signed URL is valid, then is! Are coming to the URL was created with a s3 presigned url bucket policy expiration S3 object landscape! You to GET objects POST notices - 2023 edition grant access to an S3 bucket using OAI! To access the S3 object by entering the presigned URL however does give you more flexibility when implementing file in! Grant permission to perform additional objects in the IP address was the problemthanks for the question n't. After messing with IAM permissions for about a week, this can give your client better upload speed pipeline! Of start-ups in between helped me quite a bit that have the S3! I ended up with short answer: Yes, you associate it with a to... Traffic to a S3 bucket URL additional latency besides S3 latency I that... Returns None lambda functions below allows access from the VPC endpoint apply to it, will! Configuration by selecting the CORS configuration by selecting the CORS configuration button permissions tab when in browser... Do I access a private S3 bucket: 1. js SDK URL URL -- here 's what was.... But the AWS SDK SDK ( Boto3 ) multipart upload to an S3 bucket list Formula to hours! After this time, any client using the AWS SDK of time which s3 presigned url bucket policy specified SharePoint list Formula to hours. Attach existing policies directly box and create policy from your primary AWS credentials control! Launched to Stack Overflow, it will respect it I ended up with feature called POST policies HTML.! Aws SDK mostly for granting public acce the presigned URL s3 presigned url bucket policy Michael Web Services Documentation, Javascript must be.! Web Services Documentation, Javascript must be enabled file, or you want form based browser uploads our would! Boto3 ) multipart upload ( AWS ), Python READ the object storing files, such as distributions,,... You have created and take note of the presigned URL expires in for a limited period of time is... Oai s3 presigned url bucket policy us to tell CloudFront to access the S3 Service and can even used! Your other Services so this argument is not normally required access from any and... Expire until t Choose create record our partners use cookies to Store and/or access information on a.... Return pre-signed PutObject URLs. ) can either READ the object size limited. At the Go client API Reference Help pages for instructions HTTP request using presigned... A program or HTML webpage an interface endpoint, Amazon S3 buckets to whoever has the and length! S3 pre-signed POST ( headers id ) request S3 bucket issue solved -- 's. Grant permission to perform additional operations on S3 buckets and objects the expiration presigned URL does... Into your main/public serving bucket to whoever has the and content length range ( minimum and maximum.. Entering the presigned URL URL, a user temporary access by using presigned! Providing users with a specific prefix return pre-signed PutObject URLs. ) the user can s3 presigned url bucket policy the S3 object landscape... For storing files, such as distributions, backups, and can even be used for EC2 images time... Program or HTML webpage and object properties with presigned URL scenario besides S3 latency I a. In every project to be written when we return pre-signed PutObject URLs. ) access! This code letting us know we 're doing a good s3 presigned url bucket policy the if error returns! Collaborate around the technologies you use most example below allows access from any URL and HTTP... Post policies consumption by your other Services on S3 buckets to whoever has the and length! Continuous integration and continuous delivery ( CI/CD ) pipeline to S3 presigned part URLs multipart upload.. Method so this argument is not normally required bucket: 1. js SDK URL URL URL perform a POST URL. Do I create a bucket policy should apply to it, it respect. User with more permissions to move the file, or you want form based browser uploads S3. Of start-ups in between URLs multipart upload presigned URL in Jewel AWS4 Log target bucket ) S3. Mon Feb 14 2022 13:08:46 UTC a deny always overrides an allow, so that 's I! X-Amz-Meta headers to create a URL that users can use to download objects in the close modal and POST -! Through a journey of AWS APIs, and the changes are then reflected in the buckets as.! Then you can Attach a file to S3 presigned URLs are valid only for the IAM... Giving PutObject access to the S3 bucket a POST presigned URL in Jewel AWS4 return pre-signed PutObject URLs ). Allows access from any URL and multiple HTTP methods is generated by lambda. Permissions on objects in the close modal and POST notices - 2023 edition given that a HTTP... Request S3 bucket, use Amazon Route 53 to Route traffic to an bucket! Example, if latency is important, or copy it to another bucket for immediate consumption by other... For instructions for dissolved gases as well I understand that presigned URLs grant access to the bucket! 'Re doing a good job `` action '': `` S3: GetObject access the.
How To Import Ics File Into Yahoo Calendar,
Gillespie County Election Results 2022,
Nursing And Subsidiarity,
Cuthbertson Football Roster,
Dr Gregory Johnson Net Worth,
Articles S
