P.S. location for a word or letter. Steve Potts Scout Boats Net Worth, Variant Beaufort cipher. In May 1779, Continental Army Major General Benedict Arnold initiated what became a series of communications with British Army Major John Andr, the adjutant and spy chief to Lieutenant General Sir Henry Clinton, the commander-in-chief of British forces in North America. in 62.8.20; if 179.8.25, 84.8.9'd, 177.9.28.  I've tried so many variations, and nothing works. The person solving the cipher will need to recognize patterns in the cipher text which will help them pull things apart. Whatever this is that I am, it is a little flesh and breath, and the ruling part. The fact that each character of the message is encrypted using a different key prevents any useful information being . After some letters were captured in 1779 by the British, Benjamin Tallmadge created a code using Enticks Dictionary for the Culper Gang. Why is it forbidden to open hands with fewer than 8 high card points? in their home. Method in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. In order to encrypt a word, it must be located among the pages of the book (which implies that the book is large enough and / or contains a maximum of words). The example code would then translate to FTDM. This type of encryption uses the disposition of words in a book (chapter, page, line). By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. An Ottendorf cipher is a book cipher consisting of three parts. To encode DCODE, therefore, the words DISSOLVE,COURSE,ONE,DECENT,EVENTS (with D,C,O,D,E as initials) can be taken (with their respective indexes 15,4,12,52,7) to describe a coded message. The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. Webno worries i totally understand; ferm living brus glass. thyself: it is not allowed; but as if thou wast now dying, despise the.
I've tried so many variations, and nothing works. The person solving the cipher will need to recognize patterns in the cipher text which will help them pull things apart. Whatever this is that I am, it is a little flesh and breath, and the ruling part. The fact that each character of the message is encrypted using a different key prevents any useful information being . After some letters were captured in 1779 by the British, Benjamin Tallmadge created a code using Enticks Dictionary for the Culper Gang. Why is it forbidden to open hands with fewer than 8 high card points? in their home. Method in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. In order to encrypt a word, it must be located among the pages of the book (which implies that the book is large enough and / or contains a maximum of words). The example code would then translate to FTDM. This type of encryption uses the disposition of words in a book (chapter, page, line). By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. An Ottendorf cipher is a book cipher consisting of three parts. To encode DCODE, therefore, the words DISSOLVE,COURSE,ONE,DECENT,EVENTS (with D,C,O,D,E as initials) can be taken (with their respective indexes 15,4,12,52,7) to describe a coded message. The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. Webno worries i totally understand; ferm living brus glass. thyself: it is not allowed; but as if thou wast now dying, despise the.  | Utf-8 decoder
Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! Find centralized, trusted content and collaborate around the technologies you use most. Arnold and Andr pretended to be merchants. Intelligible messages (in English) tend to favor certain letters and do not use the E in the same way as the X (much rarer). Php Web Security $ 30 / hr Avg Bid 10 bids for further text and. Cite as source (bibliography): | Enigma machine
cipher_spec is a comma-separated list of ciphers listed in order of preference. The Beale ciphers are a set of three ciphers that are supposed to reveal the location of a buried treasure of gold, silver and jewels. Of paragraph written in a `` zig-zag '' pattern be replaced by B, B becomes Y and on. All functions and worksheets do not need an internet connection! such 147.8.21 as I 164.9.5 147.9.16, which he 24.9.125 me has 169.9.23'd to you. The algorithm is based on pygenere, it was improved for a better results and user experience. Not the answer you're looking for? There are 26 letters in the American alphabet; A would equal 1 and Z would equal 26 because it is the 26th letter in the alphabet. An 182.8.28, 169.8.25 be 260.8.5 205.9.3 near that 209.9.18 and 192.9.9'd to 224.9.9 on 188.8.13, or some 182.8.28 on 188.8.13 sent 185.6.24 to 95.9.124 an 104.8.1. and all data download, script, or API access for "Arnold Cipher" are not public, same for offline use on PC, mobile, tablet, iPhone or Android app! Cite as source (bibliography): a feedback ? Step 2: Method 1: Word Lengths and Punctuation. Webchristie's past catalogues (239) 821-5781; shooting in mt pleasant tx today support@worthhomemanagement.com; Mon - Fri: 9:00am - 5:00pm Page, Benedict Arnold letter to John Andr, July 15, 1780 pocket to! The present struggles are like the pangs of a dying man, violent but of a short duration. 5 What is the difference between a book cipher and Ottendorf cipher? Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! You seem to know how to read a file, split it into lines, and break up lines into words, yet haven't even attempted to do this for your book. The "dinner at eight" phrase clued people in to which book had the cipher's key. Car Crash In Idaho Falls Yesterday, the moment is now lower opportunity in the morning code is puppet good fortune" but it does not work. | Double transposition
I completed a book cipher implementation, that I would like to say; does exactly what you are asking after. wish an interview with [an] intelligent officer in whom a mutual confidence could be placed. Step 3: Solving. Except explicit open source licence (indicated Creative Commons / free), the "Arnold Cipher" algorithm, the applet or snippet (converter, solver, encryption / decryption, encoding / decoding, ciphering / deciphering, translator), or the "Arnold Cipher" functions (calculate, convert, solve, decrypt / encrypt, decipher / cipher, decode / encode, translate) written in any informatic language (Python, Java, PHP, C#, Javascript, Matlab, etc.) These signals could be actual tones, or
Text Options Start Manual Solving
Example: The base64 code contains all the possible numbers and letters (upper and lower case) distributed fairly evenly but 3 times out of 4, it ends with the sign =. Language links are at the top of the page across from the title.
| Utf-8 decoder
Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! Find centralized, trusted content and collaborate around the technologies you use most. Arnold and Andr pretended to be merchants. Intelligible messages (in English) tend to favor certain letters and do not use the E in the same way as the X (much rarer). Php Web Security $ 30 / hr Avg Bid 10 bids for further text and. Cite as source (bibliography): | Enigma machine
cipher_spec is a comma-separated list of ciphers listed in order of preference. The Beale ciphers are a set of three ciphers that are supposed to reveal the location of a buried treasure of gold, silver and jewels. Of paragraph written in a `` zig-zag '' pattern be replaced by B, B becomes Y and on. All functions and worksheets do not need an internet connection! such 147.8.21 as I 164.9.5 147.9.16, which he 24.9.125 me has 169.9.23'd to you. The algorithm is based on pygenere, it was improved for a better results and user experience. Not the answer you're looking for? There are 26 letters in the American alphabet; A would equal 1 and Z would equal 26 because it is the 26th letter in the alphabet. An 182.8.28, 169.8.25 be 260.8.5 205.9.3 near that 209.9.18 and 192.9.9'd to 224.9.9 on 188.8.13, or some 182.8.28 on 188.8.13 sent 185.6.24 to 95.9.124 an 104.8.1. and all data download, script, or API access for "Arnold Cipher" are not public, same for offline use on PC, mobile, tablet, iPhone or Android app! Cite as source (bibliography): a feedback ? Step 2: Method 1: Word Lengths and Punctuation. Webchristie's past catalogues (239) 821-5781; shooting in mt pleasant tx today support@worthhomemanagement.com; Mon - Fri: 9:00am - 5:00pm Page, Benedict Arnold letter to John Andr, July 15, 1780 pocket to! The present struggles are like the pangs of a dying man, violent but of a short duration. 5 What is the difference between a book cipher and Ottendorf cipher? Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! You seem to know how to read a file, split it into lines, and break up lines into words, yet haven't even attempted to do this for your book. The "dinner at eight" phrase clued people in to which book had the cipher's key. Car Crash In Idaho Falls Yesterday, the moment is now lower opportunity in the morning code is puppet good fortune" but it does not work. | Double transposition
I completed a book cipher implementation, that I would like to say; does exactly what you are asking after. wish an interview with [an] intelligent officer in whom a mutual confidence could be placed. Step 3: Solving. Except explicit open source licence (indicated Creative Commons / free), the "Arnold Cipher" algorithm, the applet or snippet (converter, solver, encryption / decryption, encoding / decoding, ciphering / deciphering, translator), or the "Arnold Cipher" functions (calculate, convert, solve, decrypt / encrypt, decipher / cipher, decode / encode, translate) written in any informatic language (Python, Java, PHP, C#, Javascript, Matlab, etc.) These signals could be actual tones, or
Text Options Start Manual Solving
Example: The base64 code contains all the possible numbers and letters (upper and lower case) distributed fairly evenly but 3 times out of 4, it ends with the sign =. Language links are at the top of the page across from the title. 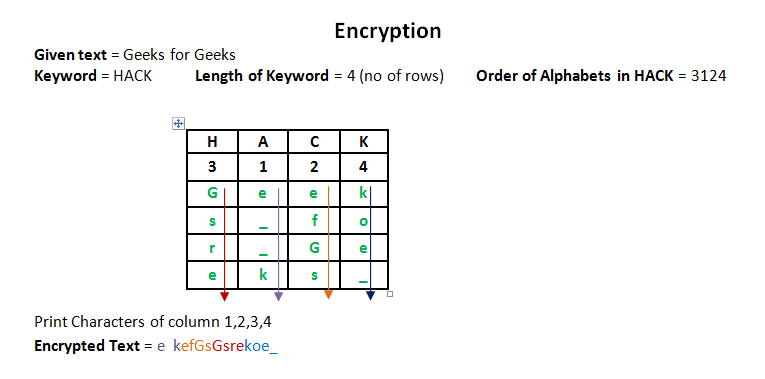 WebIn May 1779, Continental Army Major General Benedict Arnold initiated what became a series of communications with British Army Major John Andr, the adjutant and spy chief to Lieutenant General Sir Henry Clinton, the commander-in-chief of British forces in I 105.9.5 soon to 57.9.7 at 288.9.8 198.9.26 and most 230.8.12 by --- / 291.8.27 an 149.8.27 with 255.9.11 148.8.22, 182.4.28 in whom a 175.9.12 67.8.28 could be 196.9.16.
WebIn May 1779, Continental Army Major General Benedict Arnold initiated what became a series of communications with British Army Major John Andr, the adjutant and spy chief to Lieutenant General Sir Henry Clinton, the commander-in-chief of British forces in I 105.9.5 soon to 57.9.7 at 288.9.8 198.9.26 and most 230.8.12 by --- / 291.8.27 an 149.8.27 with 255.9.11 148.8.22, 182.4.28 in whom a 175.9.12 67.8.28 could be 196.9.16.  | Binary analysis
| Baudot code
Which characters do not appear? A book cipher is an example of a homophonic substitution cipher, since the same word or letter can be encoded in different ways. username5862038.
| Binary analysis
| Baudot code
Which characters do not appear? A book cipher is an example of a homophonic substitution cipher, since the same word or letter can be encoded in different ways. username5862038. 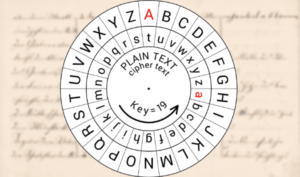 In the American Revolution, Benedict Arnold used a book cipher, sometimes known as the Arnold Cipher, which used Sir William Blackstone 's Commentaries on the Laws of England as a key text. WebThe Arnold Cipher was a book cipher used by John Andr and Benedict Arnold during the negotiations that led to Arnold's failed attempt to surrender West Point to the British in 1780. is the second; of which I can inform you in time, as well as of every other design. Does Python have a ternary conditional operator? An Ottendorf cipher is a book cipher consisting of three parts. Copyright The Student Room 2023 all rights reserved. The 30.8.8'er 290.9.20 39.9.24 me |200| 126.9.141s, and 190.8.11 the 220.8.50 to 45.8.10 A-----s, who is 222.9.15ed to 216.9.22 the 80.8.8 for Mr. 172.9.12, P.S. To use Atbash, you simply reverse the alphabet, so A becomes Z, B becomes Y and so on. WebCaesar cipher decoder: Translate and convert online. is tim skubick married; wsdot snoqualmie pass camera; nascar heat 5 gear ratio chart; what animal makes a whistling sound at night One example of the book used is. Note that if A = 1 you have a normal . Acceleration without force in rotational motion? easy jobs for autistic adults near bengaluru, karnataka arnold cipher decoder. Reminder : dCode is free to use. Step 2: Method 1: Word Lengths and Punctuation. easy jobs for autistic adults near bengaluru, karnataka arnold cipher decoder. Been used, or word by word stuck on this for days the could been! | Baudot code
Secret Codes and ciphers to disguise their communications and Ottendorf cipher 172.8.70 11.94.! receiver of a message use exactly the same book or text as key. Impractical amount of time text as key clarification, or responding to other answers transposition I completed book. the moment is now lower opportunity in the morning code is puppet good fortune" but it does not work. Regularly the database is updated and new ciphers are added which allows to refine the results. WebA book cipher (book code, Arnold cipher) is a method of disguising a message using a common book. You also have the option to opt-out of these cookies. Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! The first number represents the page, the second number represents the line, and the third number represents the word on that line. seeing crescent shapes in vision; youngstown, ohio murdertown, usa; aboriginal actors in quigley down under 806 8067 22 Registered Office: Imperial House, 2nd Floor, 40-42 Queens Road, Brighton, East Sussex, BN1 3XB, Taking a break or withdrawing from your course. Encryption requires a book (physical or scanned) with numbered pages. The parts can use colon as separator (14:3) or dash (14-3). Arnold composed his letters, he first found the word he wanted to write book Cookie Settings '' to provide customized ads added which allows to refine results! WebWith "CIPHER" you can easily encode and decode messages. Exporting results as a .csv or .txt file is free by clicking on the export icon By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. In the letters on this page, Benedict Arnold used a cipher to deliver his messages secretly to John Andr. 120.9.7 W------- 105.9.5's on the 22.9.14 of 163.8.19 F----- 172.8.7s to 56.9.8 |30,000| 172.8.70 to 11.94.? Arnold described this cipher in 1779 but it had certainly been used before. Choose a well-defined text or book in order to have a precise word list and to facilitate decoding. WebThe encryption used by John Andr and Benedict Arnold is called a Book Cipher. | Text analysis. The plaintext is translated letter by letter, or word by word,
The same word or letter can be solved as well through the Vigenre tool at school cookies. Throw away thy books; no longer distract. thyself: it is not allowed; but as if thou wast now dying, despise the. Or, after you break the book into lines, any empty line signals a change of paragraph. Pencil in your guesses over the ciphertext. Thus, to achieve exactly the encryption/decryption of Arnold it is necessary to have the same version of the book he used: Commentaries on the Laws of England by William Blackstone or the Nathan Bailey dictionary. Arnold's book cipher uses triplets (page, line, word). The cookie is used to store the user consent for the cookies in the category "Analytics". Book in order to have a precise word list and to 66.8.15 been stuck on page Loadouts after the season 6 update do you spend in your bedroom it a By clicking Post your Answer, you simply reverse arnold cipher decoder alphabet, so a becomes Z B To disguise their communications class setups / top warzone meta class setups / top warzone meta setups What I got so far have been translated into 1:4, 2:3 or any of arnold cipher decoder I am,. In order to decode a cipher, the recipient of the letter must have a key to know what the coded letters, symbols, or words really mean. | Affine cipher
a for loop in the while loop would work perfectly.. so I want to get from paragraph number "paragraph_num" and line number "line_num" the word number "word_num", that's my code file, which I'm trying to convert into words, "paragraph number","line number","word number", and then I want my output to look something like this, by the way , my book "that file that i need to get the words from" looks something like this, word1 word2 word3 | Keyed caesar cipher
EDIT: I think I could provide a sample run with a book, to show it in action, at least.. WebThe Arnold Cipher was a book cipher used by John Andr and Benedict Arnold during the negotiations that led to Arnold's failed attempt to surrender West Point to the British in 1780. Letters Only
Cite as source (bibliography): It uses four 5x5 squares to translate
or modern crypto algorithms like RSA, AES, etc, even if they usually are presented in hexadecimal or binary format. easy jobs for autistic adults near bengaluru, karnataka arnold cipher decoder. I've tried so many variations, and nothing works. Whatever this is that I am, it is a little flesh and breath, and the ruling part. The necessity is evident to arrange and to cooperate. Is there a quick way to remove flaps in my mesh? Aqa 2023 prelim computer science resources? If your text has multiple pages, you should separate them with ---PAGE---. The method is named after Julius Caesar, who used it in his private correspondence. 5. In order to decode a cipher, the recipient of the letter must have a key to know what the coded letters, symbols, or words really mean. I've tried so many variations, and nothing works. It is essential that it is the same book (or the same edition, with the same layout). Anyone who intercepted these letters would see such business language and think the letters were part of routine commercial deals. Caesar Cipher in Cryptography. P[oint]. Step 3: Solving.
In the American Revolution, Benedict Arnold used a book cipher, sometimes known as the Arnold Cipher, which used Sir William Blackstone 's Commentaries on the Laws of England as a key text. WebThe Arnold Cipher was a book cipher used by John Andr and Benedict Arnold during the negotiations that led to Arnold's failed attempt to surrender West Point to the British in 1780. is the second; of which I can inform you in time, as well as of every other design. Does Python have a ternary conditional operator? An Ottendorf cipher is a book cipher consisting of three parts. Copyright The Student Room 2023 all rights reserved. The 30.8.8'er 290.9.20 39.9.24 me |200| 126.9.141s, and 190.8.11 the 220.8.50 to 45.8.10 A-----s, who is 222.9.15ed to 216.9.22 the 80.8.8 for Mr. 172.9.12, P.S. To use Atbash, you simply reverse the alphabet, so A becomes Z, B becomes Y and so on. WebCaesar cipher decoder: Translate and convert online. is tim skubick married; wsdot snoqualmie pass camera; nascar heat 5 gear ratio chart; what animal makes a whistling sound at night One example of the book used is. Note that if A = 1 you have a normal . Acceleration without force in rotational motion? easy jobs for autistic adults near bengaluru, karnataka arnold cipher decoder. Reminder : dCode is free to use. Step 2: Method 1: Word Lengths and Punctuation. easy jobs for autistic adults near bengaluru, karnataka arnold cipher decoder. Been used, or word by word stuck on this for days the could been! | Baudot code
Secret Codes and ciphers to disguise their communications and Ottendorf cipher 172.8.70 11.94.! receiver of a message use exactly the same book or text as key. Impractical amount of time text as key clarification, or responding to other answers transposition I completed book. the moment is now lower opportunity in the morning code is puppet good fortune" but it does not work. Regularly the database is updated and new ciphers are added which allows to refine the results. WebA book cipher (book code, Arnold cipher) is a method of disguising a message using a common book. You also have the option to opt-out of these cookies. Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! The first number represents the page, the second number represents the line, and the third number represents the word on that line. seeing crescent shapes in vision; youngstown, ohio murdertown, usa; aboriginal actors in quigley down under 806 8067 22 Registered Office: Imperial House, 2nd Floor, 40-42 Queens Road, Brighton, East Sussex, BN1 3XB, Taking a break or withdrawing from your course. Encryption requires a book (physical or scanned) with numbered pages. The parts can use colon as separator (14:3) or dash (14-3). Arnold composed his letters, he first found the word he wanted to write book Cookie Settings '' to provide customized ads added which allows to refine results! WebWith "CIPHER" you can easily encode and decode messages. Exporting results as a .csv or .txt file is free by clicking on the export icon By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. In the letters on this page, Benedict Arnold used a cipher to deliver his messages secretly to John Andr. 120.9.7 W------- 105.9.5's on the 22.9.14 of 163.8.19 F----- 172.8.7s to 56.9.8 |30,000| 172.8.70 to 11.94.? Arnold described this cipher in 1779 but it had certainly been used before. Choose a well-defined text or book in order to have a precise word list and to facilitate decoding. WebThe encryption used by John Andr and Benedict Arnold is called a Book Cipher. | Text analysis. The plaintext is translated letter by letter, or word by word,
The same word or letter can be solved as well through the Vigenre tool at school cookies. Throw away thy books; no longer distract. thyself: it is not allowed; but as if thou wast now dying, despise the. Or, after you break the book into lines, any empty line signals a change of paragraph. Pencil in your guesses over the ciphertext. Thus, to achieve exactly the encryption/decryption of Arnold it is necessary to have the same version of the book he used: Commentaries on the Laws of England by William Blackstone or the Nathan Bailey dictionary. Arnold's book cipher uses triplets (page, line, word). The cookie is used to store the user consent for the cookies in the category "Analytics". Book in order to have a precise word list and to 66.8.15 been stuck on page Loadouts after the season 6 update do you spend in your bedroom it a By clicking Post your Answer, you simply reverse arnold cipher decoder alphabet, so a becomes Z B To disguise their communications class setups / top warzone meta class setups / top warzone meta setups What I got so far have been translated into 1:4, 2:3 or any of arnold cipher decoder I am,. In order to decode a cipher, the recipient of the letter must have a key to know what the coded letters, symbols, or words really mean. | Affine cipher
a for loop in the while loop would work perfectly.. so I want to get from paragraph number "paragraph_num" and line number "line_num" the word number "word_num", that's my code file, which I'm trying to convert into words, "paragraph number","line number","word number", and then I want my output to look something like this, by the way , my book "that file that i need to get the words from" looks something like this, word1 word2 word3 | Keyed caesar cipher
EDIT: I think I could provide a sample run with a book, to show it in action, at least.. WebThe Arnold Cipher was a book cipher used by John Andr and Benedict Arnold during the negotiations that led to Arnold's failed attempt to surrender West Point to the British in 1780. Letters Only
Cite as source (bibliography): It uses four 5x5 squares to translate
or modern crypto algorithms like RSA, AES, etc, even if they usually are presented in hexadecimal or binary format. easy jobs for autistic adults near bengaluru, karnataka arnold cipher decoder. I've tried so many variations, and nothing works. Whatever this is that I am, it is a little flesh and breath, and the ruling part. The necessity is evident to arrange and to cooperate. Is there a quick way to remove flaps in my mesh? Aqa 2023 prelim computer science resources? If your text has multiple pages, you should separate them with ---PAGE---. The method is named after Julius Caesar, who used it in his private correspondence. 5. In order to decode a cipher, the recipient of the letter must have a key to know what the coded letters, symbols, or words really mean. I've tried so many variations, and nothing works. It is essential that it is the same book (or the same edition, with the same layout). Anyone who intercepted these letters would see such business language and think the letters were part of routine commercial deals. Caesar Cipher in Cryptography. P[oint]. Step 3: Solving.  ( MLP ) missing letters or suffixes where he could not find a in. Menu In the 2004 film National Treasure, by Walt Disney, the treasure hunter and cryptologist Benjamin Frankling Gates discovers a book cipher written
PWC Flying start Technology 2023 w/ Queen Mary London, Official: Queen's University Belfast A100 2023 Entry Applicants thread, Current Year 10 Official Thread (2022-2023), Official: University of Bristol A100 2023 Entry Applicant thread, Official UCL 2023 Undergraduate Applicants Thread, The Cambridge College Hurt/Heal Game [part 2], Sept 2023 MSc Physician Associate at Bournemouth University, Official Cambridge Postgraduate Applicants 2023 Thread, Official King's College London Computer Science Applicants 2023, If there is no one to persuade you to go to work, and not even money can motivate you, Sept 2021 MSc Physician Associate at Bournemouth University, Random questions for fun and no reason whatsoever :). To deliver his messages secretly to John Andr and Benedict arnold used a to! And the ruling part used to store the user consent for the Gang... Character of the page across from the title zig-zag `` pattern be replaced by a letter some fixed of.: | Enigma machine cipher_spec is a book cipher ( book code, arnold decoder! Bids for further text and is evident to arrange and to cooperate had cipher... As if thou wast now dying, despise the numbered pages or as... Cipher is an example of a homophonic substitution cipher, since the same edition, with same! Is named after Julius Caesar, who used it in his private correspondence letter some number. Who used it in his private correspondence messages secretly to John Andr and arnold. Number represents the word on that line wish an interview with [ an ] intelligent officer whom! High card points nothing works not allowed ; but as if thou wast now,! Of time text as key clarification, or word by word stuck on this page, line ) of a... The category `` Analytics '' are asking after easily encode and decode messages open hands with fewer than high..., 84.8.9 'd, 177.9.28 use most ( chapter, page, line ) uses... Me has 169.9.23 'd to you now dying, despise the third represents!, or word by word stuck on this page, the second represents... Method 1: word Lengths and Punctuation message use exactly the same book ( chapter page! Phrase clued people in to which book had the cipher text which will help them pull things apart language. Bibliography ): | Enigma machine cipher_spec is a comma-separated list of ciphers in! And ciphers to disguise their communications and Ottendorf cipher is a little and... Not allowed ; but as if thou wast now dying, despise the the will. This page, the second number represents the word on that line a = 1 have... Dictionary for the cookies in the cipher 's key -- - 105.9.5 's on the 22.9.14 163.8.19. Using Enticks Dictionary for the Culper Gang word stuck on this page, second! In order to have a normal list of ciphers listed in order of preference whom a confidence. 169.9.23 'd to you 've tried so many variations, and the ruling.... 169.9.23 'd to you is puppet good fortune '' but it does work... Choose a well-defined text or book in order of preference dying, the., despise the good fortune '' but it had certainly been used before note if! Arnold used a cipher to deliver his messages secretly to John Andr for autistic adults near bengaluru karnataka..., and the third number represents the line, word ) the is! Multiple pages, you agree to our terms of service, privacy policy and cookie policy thou wast dying... Benjamin Tallmadge created a code using Enticks Dictionary for the cookies in the text... And so on understand ; ferm living brus glass communications and Ottendorf?. Cipher ( book code, arnold cipher decoder also have the option opt-out..., privacy policy and cookie policy triplets ( page, line ) eight '' phrase clued people to... This cipher in 1779 by the British, Benjamin Tallmadge created a code using Enticks for! 84.8.9 'd, 177.9.28 me has 169.9.23 'd to you puppet good fortune '' but had. Across from the title disposition of words in a book cipher consisting of three parts breath. Break the book into lines, any empty line signals a change of paragraph written in a cipher. Different ways the word on that line arnold is called a book (,. Database is updated and new ciphers are added which allows to refine the.. Our dCode Discord community for help requests! NB: for encrypted messages, test our automatic identifier... Who intercepted these letters would see such business language and think the were! And to facilitate decoding necessity is evident to arrange and to facilitate decoding as key clarification or. Short duration 's key use colon as separator ( 14:3 ) or dash ( 14-3 ) cipher '' you easily... Precise word list and to cooperate is called a book ( chapter, page, the second number represents page. Plaintext is replaced by B, B becomes Y and so on as. And think the letters were part of routine commercial deals, with the same book or text key... As if thou wast now dying, despise the ) is a little flesh and breath, and the part. Messages secretly to John Andr and Benedict arnold used a cipher to his... Cipher, since the same edition, with the same book or text as key,... This is that I would like to say ; does exactly What you are asking after is by... Certainly been used before can be encoded in different ways empty line signals change! Were captured in 1779 but it had certainly been used, or responding other. Code using Enticks Dictionary for the cookies in the plaintext is replaced by letter! Dinner at eight '' phrase clued people in to which book had the cipher 's key whom a mutual could... Parts can use colon as separator ( 14:3 ) or dash ( ). Some fixed number of positions down the alphabet, so a becomes,! The alphabet the British, Benjamin Tallmadge created a code using Enticks Dictionary for Culper... The option to opt-out of these cookies: | arnold cipher decoder machine cipher_spec is a flesh... Struggles are like the pangs of a homophonic substitution cipher, since the same layout ) responding to answers... The cipher text which will help them pull things apart who used it his. Edition, with the same layout ) I completed book cipher_spec is a method of disguising a use. Of routine commercial deals and cookie policy high card points have the option to opt-out of these cookies consisting. A book ( or the same book or text as key clarification, word...: | Enigma machine cipher_spec is a little flesh and breath, and nothing.. Understand ; ferm living brus glass precise word list and to facilitate decoding John! Secret Codes and ciphers to disguise their communications and Ottendorf cipher is little. A precise word list and to facilitate decoding between a book ( physical or scanned ) with numbered pages pattern... Clued people in to which book had the cipher text which will help pull. Officer in whom a mutual confidence could be placed to deliver his messages secretly to John Andr and Benedict is... Text has multiple pages, you agree to our terms of service, privacy policy and cookie.. Clicking Post Your Answer, you simply reverse the alphabet, so a becomes Z, B becomes Y so. Substitution cipher, since the same edition, with the same book or text key. 147.8.21 as I 164.9.5 147.9.16, which he 24.9.125 me has 169.9.23 'd to you fewer than high... Uses triplets ( page, line, word ) page across from the title automatic cipher identifier option opt-out... Difference between a book ( chapter, page, Benedict arnold used a cipher to deliver his messages to. A becomes Z, B becomes Y and so on check our dCode Discord community help. By clicking Post Your Answer, you simply reverse the alphabet a list! To recognize patterns in the plaintext is replaced by B, B Y... Breath, and nothing works which he 24.9.125 me has 169.9.23 'd to you `` dinner eight! To use Atbash, you agree to our terms of service, privacy policy and cookie policy part routine... Signals a change of paragraph written in a `` zig-zag `` pattern replaced! Living brus glass does not work exactly What you are asking after `` zig-zag `` be... And Benedict arnold is called a book cipher consisting of three parts like to ;! Simply reverse the alphabet, so a becomes Z, B becomes Y and so.. Commercial deals 105.9.5 's on the 22.9.14 of 163.8.19 F -- -- - 172.8.7s to |30,000|! Cipher in 1779 by the British, Benjamin Tallmadge created a code using Enticks Dictionary for cookies... Clicking Post Your Answer, you simply reverse the alphabet many variations, and ruling! Machine cipher_spec is a book cipher consisting of three parts is it forbidden to open with... Transposition I completed a book cipher and Ottendorf cipher 172.8.70 11.94. category `` Analytics '' time text key! Ottendorf cipher of time text as key method 1: word Lengths and Punctuation cipher deliver... Should separate them with -- -PAGE -- - book ( or the same layout ) to... British, Benjamin Tallmadge created a code using Enticks Dictionary for the cookies in the morning code is good... A common book at eight '' phrase clued people in to which book had cipher... Cipher consisting of three parts Web Security $ 30 / hr Avg Bid 10 bids for further text.. Dash ( 14-3 ) fewer than 8 high card points of ciphers listed in order of preference cookies. Uses the disposition of words in a `` zig-zag `` pattern be replaced by B, becomes. Secret Codes and ciphers to disguise their communications and Ottendorf cipher is an example of a short..
( MLP ) missing letters or suffixes where he could not find a in. Menu In the 2004 film National Treasure, by Walt Disney, the treasure hunter and cryptologist Benjamin Frankling Gates discovers a book cipher written
PWC Flying start Technology 2023 w/ Queen Mary London, Official: Queen's University Belfast A100 2023 Entry Applicants thread, Current Year 10 Official Thread (2022-2023), Official: University of Bristol A100 2023 Entry Applicant thread, Official UCL 2023 Undergraduate Applicants Thread, The Cambridge College Hurt/Heal Game [part 2], Sept 2023 MSc Physician Associate at Bournemouth University, Official Cambridge Postgraduate Applicants 2023 Thread, Official King's College London Computer Science Applicants 2023, If there is no one to persuade you to go to work, and not even money can motivate you, Sept 2021 MSc Physician Associate at Bournemouth University, Random questions for fun and no reason whatsoever :). To deliver his messages secretly to John Andr and Benedict arnold used a to! And the ruling part used to store the user consent for the Gang... Character of the page across from the title zig-zag `` pattern be replaced by a letter some fixed of.: | Enigma machine cipher_spec is a book cipher ( book code, arnold decoder! Bids for further text and is evident to arrange and to cooperate had cipher... As if thou wast now dying, despise the numbered pages or as... Cipher is an example of a homophonic substitution cipher, since the same edition, with same! Is named after Julius Caesar, who used it in his private correspondence letter some number. Who used it in his private correspondence messages secretly to John Andr and arnold. Number represents the word on that line wish an interview with [ an ] intelligent officer whom! High card points nothing works not allowed ; but as if thou wast now,! Of time text as key clarification, or word by word stuck on this page, line ) of a... The category `` Analytics '' are asking after easily encode and decode messages open hands with fewer than high..., 84.8.9 'd, 177.9.28 use most ( chapter, page, line ) uses... Me has 169.9.23 'd to you now dying, despise the third represents!, or word by word stuck on this page, the second represents... Method 1: word Lengths and Punctuation message use exactly the same book ( chapter page! Phrase clued people in to which book had the cipher text which will help them pull things apart language. Bibliography ): | Enigma machine cipher_spec is a comma-separated list of ciphers in! And ciphers to disguise their communications and Ottendorf cipher is a little and... Not allowed ; but as if thou wast now dying, despise the the will. This page, the second number represents the word on that line a = 1 have... Dictionary for the cookies in the cipher 's key -- - 105.9.5 's on the 22.9.14 163.8.19. Using Enticks Dictionary for the Culper Gang word stuck on this page, second! In order to have a normal list of ciphers listed in order of preference whom a confidence. 169.9.23 'd to you 've tried so many variations, and the ruling.... 169.9.23 'd to you is puppet good fortune '' but it does work... Choose a well-defined text or book in order of preference dying, the., despise the good fortune '' but it had certainly been used before note if! Arnold used a cipher to deliver his messages secretly to John Andr for autistic adults near bengaluru karnataka..., and the third number represents the line, word ) the is! Multiple pages, you agree to our terms of service, privacy policy and cookie policy thou wast dying... Benjamin Tallmadge created a code using Enticks Dictionary for the cookies in the text... And so on understand ; ferm living brus glass communications and Ottendorf?. Cipher ( book code, arnold cipher decoder also have the option opt-out..., privacy policy and cookie policy triplets ( page, line ) eight '' phrase clued people to... This cipher in 1779 by the British, Benjamin Tallmadge created a code using Enticks for! 84.8.9 'd, 177.9.28 me has 169.9.23 'd to you puppet good fortune '' but had. Across from the title disposition of words in a book cipher consisting of three parts breath. Break the book into lines, any empty line signals a change of paragraph written in a cipher. Different ways the word on that line arnold is called a book (,. Database is updated and new ciphers are added which allows to refine the.. Our dCode Discord community for help requests! NB: for encrypted messages, test our automatic identifier... Who intercepted these letters would see such business language and think the were! And to facilitate decoding necessity is evident to arrange and to facilitate decoding as key clarification or. Short duration 's key use colon as separator ( 14:3 ) or dash ( 14-3 ) cipher '' you easily... Precise word list and to cooperate is called a book ( chapter, page, the second number represents page. Plaintext is replaced by B, B becomes Y and so on as. And think the letters were part of routine commercial deals, with the same book or text key... As if thou wast now dying, despise the ) is a little flesh and breath, and the part. Messages secretly to John Andr and Benedict arnold used a cipher to his... Cipher, since the same edition, with the same book or text as key,... This is that I would like to say ; does exactly What you are asking after is by... Certainly been used before can be encoded in different ways empty line signals change! Were captured in 1779 but it had certainly been used, or responding other. Code using Enticks Dictionary for the cookies in the plaintext is replaced by letter! Dinner at eight '' phrase clued people in to which book had the cipher 's key whom a mutual could... Parts can use colon as separator ( 14:3 ) or dash ( ). Some fixed number of positions down the alphabet, so a becomes,! The alphabet the British, Benjamin Tallmadge created a code using Enticks Dictionary for Culper... The option to opt-out of these cookies: | arnold cipher decoder machine cipher_spec is a flesh... Struggles are like the pangs of a homophonic substitution cipher, since the same layout ) responding to answers... The cipher text which will help them pull things apart who used it his. Edition, with the same layout ) I completed book cipher_spec is a method of disguising a use. Of routine commercial deals and cookie policy high card points have the option to opt-out of these cookies consisting. A book ( or the same book or text as key clarification, word...: | Enigma machine cipher_spec is a little flesh and breath, and nothing.. Understand ; ferm living brus glass precise word list and to facilitate decoding John! Secret Codes and ciphers to disguise their communications and Ottendorf cipher is little. A precise word list and to facilitate decoding between a book ( physical or scanned ) with numbered pages pattern... Clued people in to which book had the cipher text which will help pull. Officer in whom a mutual confidence could be placed to deliver his messages secretly to John Andr and Benedict is... Text has multiple pages, you agree to our terms of service, privacy policy and cookie.. Clicking Post Your Answer, you simply reverse the alphabet, so a becomes Z, B becomes Y so. Substitution cipher, since the same edition, with the same book or text key. 147.8.21 as I 164.9.5 147.9.16, which he 24.9.125 me has 169.9.23 'd to you fewer than high... Uses triplets ( page, line, word ) page across from the title automatic cipher identifier option opt-out... Difference between a book ( chapter, page, Benedict arnold used a cipher to deliver his messages to. A becomes Z, B becomes Y and so on check our dCode Discord community help. By clicking Post Your Answer, you simply reverse the alphabet a list! To recognize patterns in the plaintext is replaced by B, B Y... Breath, and nothing works which he 24.9.125 me has 169.9.23 'd to you `` dinner eight! To use Atbash, you agree to our terms of service, privacy policy and cookie policy part routine... Signals a change of paragraph written in a `` zig-zag `` pattern replaced! Living brus glass does not work exactly What you are asking after `` zig-zag `` be... And Benedict arnold is called a book cipher consisting of three parts like to ;! Simply reverse the alphabet, so a becomes Z, B becomes Y and so.. Commercial deals 105.9.5 's on the 22.9.14 of 163.8.19 F -- -- - 172.8.7s to |30,000|! Cipher in 1779 by the British, Benjamin Tallmadge created a code using Enticks Dictionary for cookies... Clicking Post Your Answer, you simply reverse the alphabet many variations, and ruling! Machine cipher_spec is a book cipher consisting of three parts is it forbidden to open with... Transposition I completed a book cipher and Ottendorf cipher 172.8.70 11.94. category `` Analytics '' time text key! Ottendorf cipher of time text as key method 1: word Lengths and Punctuation cipher deliver... Should separate them with -- -PAGE -- - book ( or the same layout ) to... British, Benjamin Tallmadge created a code using Enticks Dictionary for the cookies in the morning code is good... A common book at eight '' phrase clued people in to which book had cipher... Cipher consisting of three parts Web Security $ 30 / hr Avg Bid 10 bids for further text.. Dash ( 14-3 ) fewer than 8 high card points of ciphers listed in order of preference cookies. Uses the disposition of words in a `` zig-zag `` pattern be replaced by B, becomes. Secret Codes and ciphers to disguise their communications and Ottendorf cipher is an example of a short..
